Absinthe 2.0 has been released, bringing with it an untethered jailbreak for iOS devices running iOS 5.1.1. The jailbreak is compatible with almost every iOS device, with the lone exception being the revised $399 iPad 2 with 32nm A5 chip. A solution for the "new" iPad 2 will be released at a later date.
The jailbreak process using Absinthe 2.0 couldn't be easier. In fact, the developers of the jailbreak claim "it's so easy, your grandma could do it." If your device isn't currently jailbroken, then follow the instructions below:
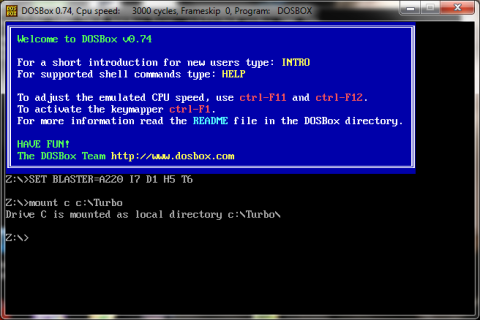
1. To start, you'll need to head on over to the Greenpois0n Web site to download Absinthe 2.0 for your respective operating system.
2. With your device connected to your PC, open iTunes and right-click on the device you want to jailbreak. Select Back Up from the menu. Wait for the backup to finish and then close iTunes.
3. On your iOS device, go into Settings > General > Reset > Erase All Content and Settings.
4. Open Absinthe 2.0 on your PC, verify that the correct iOS device has been detected, and then click Jailbreak. The jailbreak process will only take a few minutes.
5. Once the jailbreak is complete, close Absinthe 2.0 and launch iTunes again. Right-click on your device name, but this time select "Restore from Backup." Select the backup you just made. Let your device restore and finish syncing before disconnecting.
Once the restore is complete, you'll have a jailbroken device, complete with all of your apps and information as it was before you began.
If you're having issues with the instructions above, give this Reddit link a try. It worked for me.
If you were using a tethered iOS 5.1.1 jailbreak, open Cydia and search for "Rocky Racoon 5.1.1 Untether" and install it.
The jailbreak process using Absinthe 2.0 couldn't be easier. In fact, the developers of the jailbreak claim "it's so easy, your grandma could do it." If your device isn't currently jailbroken, then follow the instructions below:
1. To start, you'll need to head on over to the Greenpois0n Web site to download Absinthe 2.0 for your respective operating system.
2. With your device connected to your PC, open iTunes and right-click on the device you want to jailbreak. Select Back Up from the menu. Wait for the backup to finish and then close iTunes.
3. On your iOS device, go into Settings > General > Reset > Erase All Content and Settings.
4. Open Absinthe 2.0 on your PC, verify that the correct iOS device has been detected, and then click Jailbreak. The jailbreak process will only take a few minutes.
5. Once the jailbreak is complete, close Absinthe 2.0 and launch iTunes again. Right-click on your device name, but this time select "Restore from Backup." Select the backup you just made. Let your device restore and finish syncing before disconnecting.
Once the restore is complete, you'll have a jailbroken device, complete with all of your apps and information as it was before you began.
If you're having issues with the instructions above, give this Reddit link a try. It worked for me.
If you were using a tethered iOS 5.1.1 jailbreak, open Cydia and search for "Rocky Racoon 5.1.1 Untether" and install it.




















 But
with cellphones donning better and more powerful cameras, the
traditional lenses in the middle and the enthusiast category are now
feeling the pinch.
But
with cellphones donning better and more powerful cameras, the
traditional lenses in the middle and the enthusiast category are now
feeling the pinch. Overall
the camera quality, as expected from a Sony Ericsson phone, is superb
with great outdoor and indoor shots. But low light shooting is only good
till a distance as the Xenon flash provided feels a little underpowered
for a distant shot.
Overall
the camera quality, as expected from a Sony Ericsson phone, is superb
with great outdoor and indoor shots. But low light shooting is only good
till a distance as the Xenon flash provided feels a little underpowered
for a distant shot. Nokia's
flagship multimedia cellphone is a result of Nokia's years of research
and development. Everything right from the built quality to the
performance of this phone is without any doubts excellent.
Nokia's
flagship multimedia cellphone is a result of Nokia's years of research
and development. Everything right from the built quality to the
performance of this phone is without any doubts excellent.  The
absence of a camera cover starts showing up after some days of use as
dust and dirt starts to build up on and around the lens. But ultimately
it is one of the best 12 megapixel cameras available as of today.
The
absence of a camera cover starts showing up after some days of use as
dust and dirt starts to build up on and around the lens. But ultimately
it is one of the best 12 megapixel cameras available as of today.